Setting Up AWS Sub-Account Structure For Projects
AWS is shifting towards a system of IAM Identity Center (previously AWS SSO) federation and permission sets as recommended best practice, for setting up console/access keys. This provides temporary credentials for access for a role, instead of for IAM users. Read more here.
# Summary:
When creating a new AWS account, there are several best practices that should be applied before you start building:
- Configure MFA.
- Create a new account, to retire the root account from admin usage.
- Create an organisation unit per project.
- Apply IAM users, roles and apply least-privilege principle to account access – i.e create separate accounts for separate projects etc.
- If multiple accounts are created, make sure to utilise consolidated billing, and set-up SCPs to again apply least-privilege to accounts.
- Set up billing alarms for any used resources, especially if trying to stick to free tier.
Doing this manually and without the assistance of tools such as Terraform, CDK, Control Tower etc. is tedious, so if you’re looking to repeat the creation of these environments often, I would look into those tools.
# Steps:
# 1. Configure MFA
Root account:
- Click on the account name on the top-left, then “Security Credentials”.
- Under MFA, click “Assign MFA Device”.
- Configure preferred MFA method.
- Sign out and Sign back in to verify.
Subsequent Users:
- Head to the IAM Identity Center and enable the service with AWS Organisations.
- In the subsequent window, click on “Configure multi-factor authentication (MFA)”.
- Review the settings before saving changes. Recommend to check:
- “Require them to register an MFA device at sign in”
- Sign out of the account and sign back in to set-up MFA on root account.
# 2. Create a new IAM User admin account
Create an admin account to perform administrator duties, aside from those that require the management account. After this account is made, we mostly retire the management account.
Creating Administrator Group:
- In the IAM Console, click on Groups -> Create Group on the left-hand panel.
- Assign a group name and check the box on the provided permission policy “AdministratorAccess” (should be the top most policy in that table).
- Click Create Group at the bottom.
Creating Administrative user: This is the account to use from now on, unless organisation changes need to be made.
- Staying in the IAM Console Click on Users -> Add User.
- Set a username and password - good practice is to have that user set a new password on sign-in. Click next.
- Add that user to the previously created administrator group, and click next.
- Review the configuration and create user. Make sure to save the provided URL here for signing in.
- Sign in using the link, and repeat setting up MFA.
# 3. Creating an OU/sub-account for different projects
In essence, there should be a single management account serving to consolidate all sub-accounts. Under that, there will be a projects OU, with further sub-OUs to house each specific project, such as below:
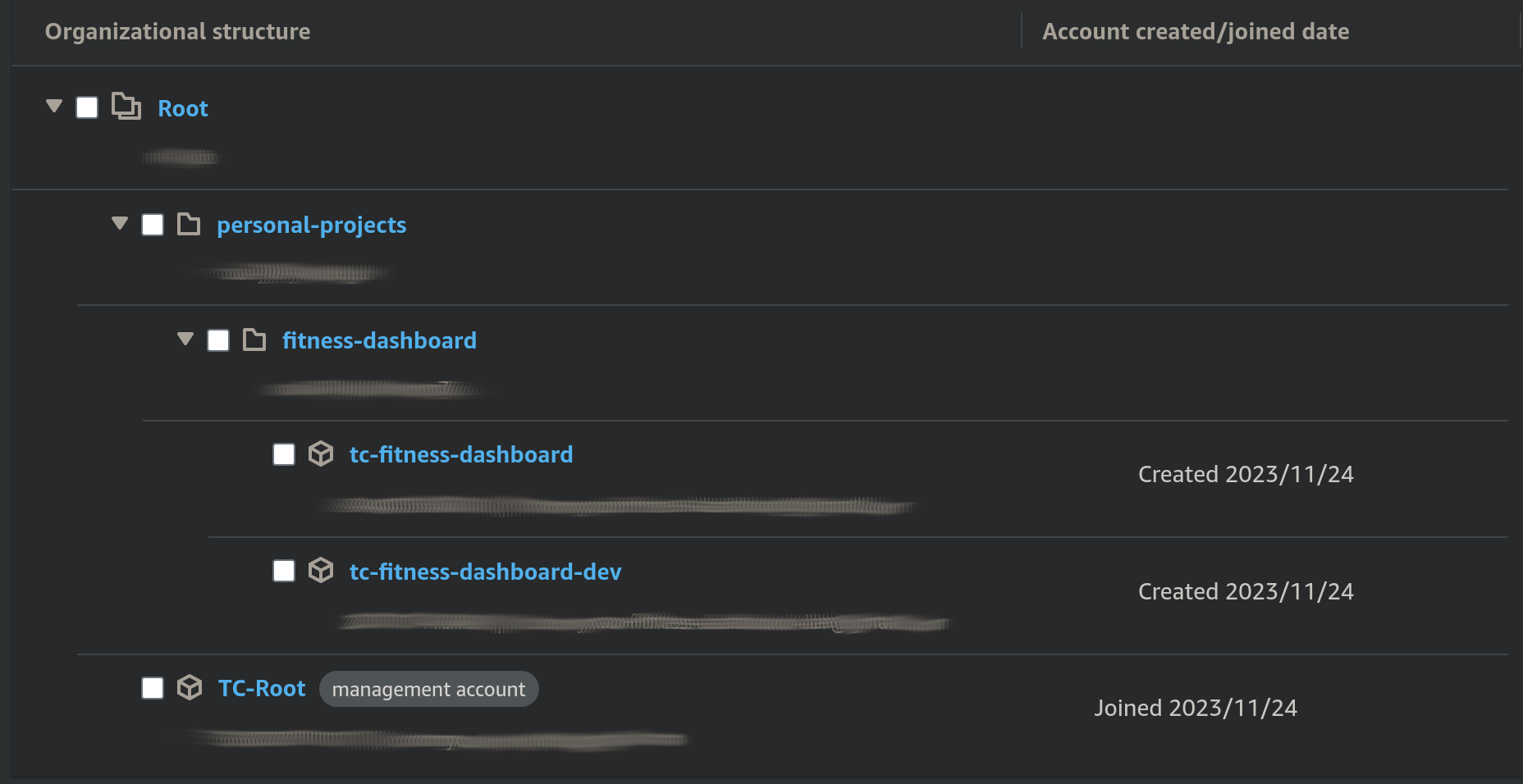
- Navigate to AWS Organisations and click on “Add an AWS account”.
- Create a new account filling in a separate email address
- Tip: If you’ve got a gmail account, you can make use of their aliasing feature to utilise a single email for multiple user accounts.
- e.g useremail@gmail.com can be used again with useremail+whateveryouwantsuffix@gmail.com.
- Open another incognito window and log into that newly created account, using the “root account” sign in options.
- Set-up MFA for this new project account!
- Navigate back to AWS Organizations, and check on the “Root” folder.
- Click on the “Actions” button top-right, and create new organisational unit (I named mine “projects”).
- Click on that newly created OU, and create another one with the specific project name, e.g above “fitness-dashboard”.
- Add new AWS accounts to that specific project OU, following best practice of a Development and Prod account.
# 4. Creating admin roles and worker roles for subsequent accounts:
For those newly created project specific accounts, we need to follow the same process of protecting the root AWS account, opting for an admin account instead.
- Follow step 2 within each of the DEV/PROD accounts, to create administrator IAM users.
- Enable MFA!
- Create one extra IAM user for each of the accounts also, to represent the “non-administrative worker”.
- Don’t attach this IAM user to the administrators group!
- e.g
fitness-dashboard-worker.
# 5. Creating IAM Roles for worker access to services
Best practice is to only provide “workers” with the specific access they require, to do their job. This is best applied through assigning access permissions to IAM Roles, based on the IAM Group the user belongs to. There are many ways to do this, but here’s a simple way using in-line policies (process is made through the admin account):
- Head to IAM -> Roles -> Create Role.
- Check box for “Trusted Entity Type”, for “AWS Account”, and “Require MFA”.
- Select the required policies, such as “AmazonEC2FullAccess”.
- Set a role name and create.
- Navigate to the worker user in IAM -> Users.
- Click “Add Permissions” under the “Permissions” tab.
- Switch the view to
JSONand add the ARNs to each of the new roles like so:- This allows the user to assume the specified roles.
| |
- Save changes!
- Note the ARN lines down for next steps in enabling switching roles.
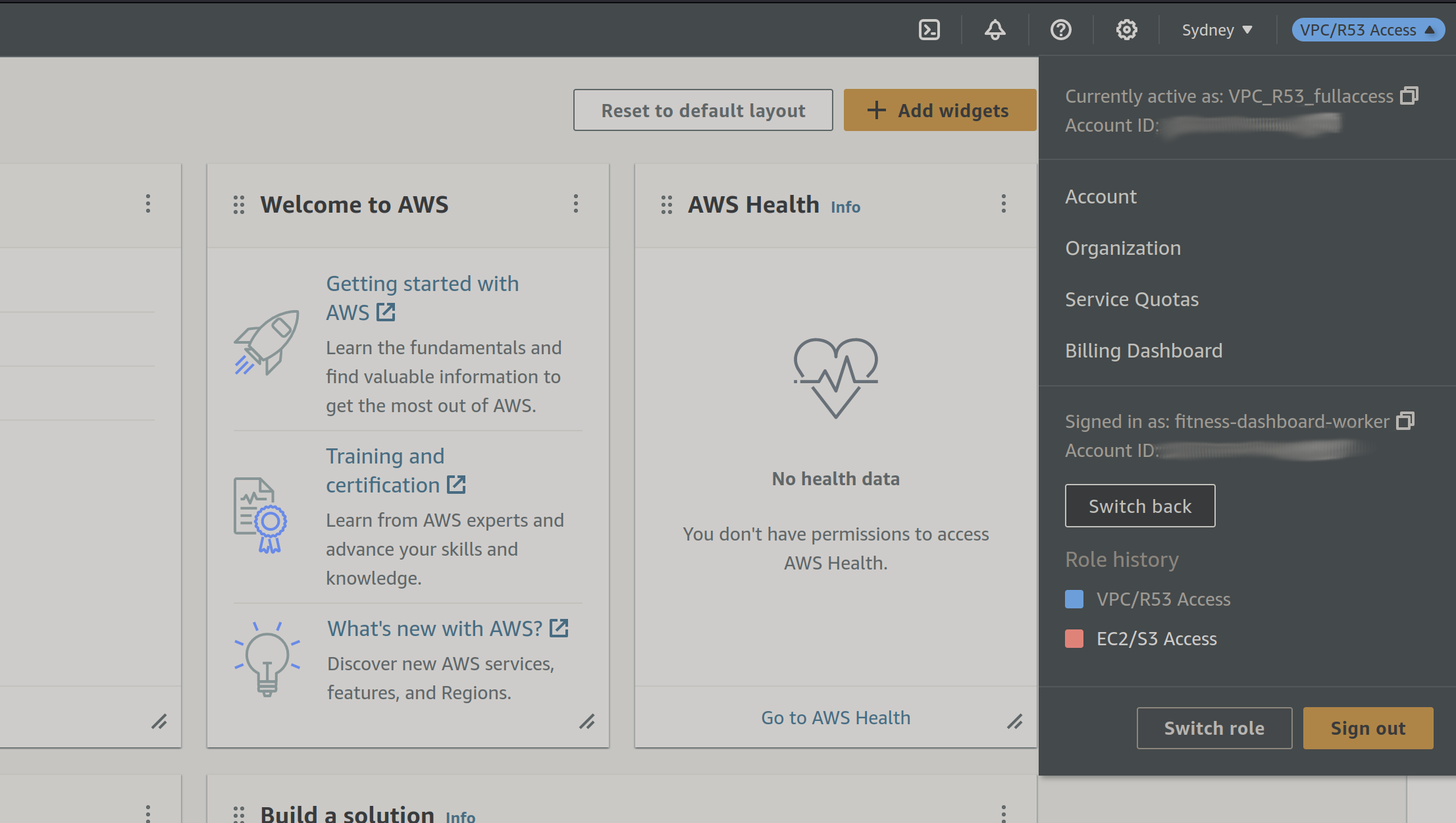
# Switching Roles:
The worker user should have access to assume both roles now, and this can conveniently done through:
- In the top-right menu, and click “Switch Role”.
- Click “Switch Role” again.
- Enter the account number and, per it’s inclusion in the ARN.
- Enter the role name under “Role”.
- The display name and colour are up to your preference.
- Click switch role. Switched roles will be shown in the top-right menu for future convenience.
# Resources:
- https://docs.aws.amazon.com/singlesignon/latest/userguide/mfa-configure.html
- https://docs.aws.amazon.com/streams/latest/dev/setting-up.html
- https://www.youtube.com/watch?v=zVJnenaD3U8
- https://mim-armand.medium.com/steps-to-create-an-aws-sub-accounts-free-tier-2268b17c9f7
- https://docs.aws.amazon.com/organizations/latest/userguide/orgs_tutorials_basic.html
- https://dev.to/aws-heroes/setting-up-a-multi-account-aws-environment-1h67
- https://www.reddit.com/r/aws/comments/109776f/how_should_individual_developers_access_devprod/
- https://www.youtube.com/watch?v=BfE2G-fsBNU